
Nathan Knight devises algorithm for packing — and perhaps more playing time

mashable.json · GitHub

FireEye Uncovers CVE-2017-8759: Zero-Day Used in the Wild to Distri - exploit database
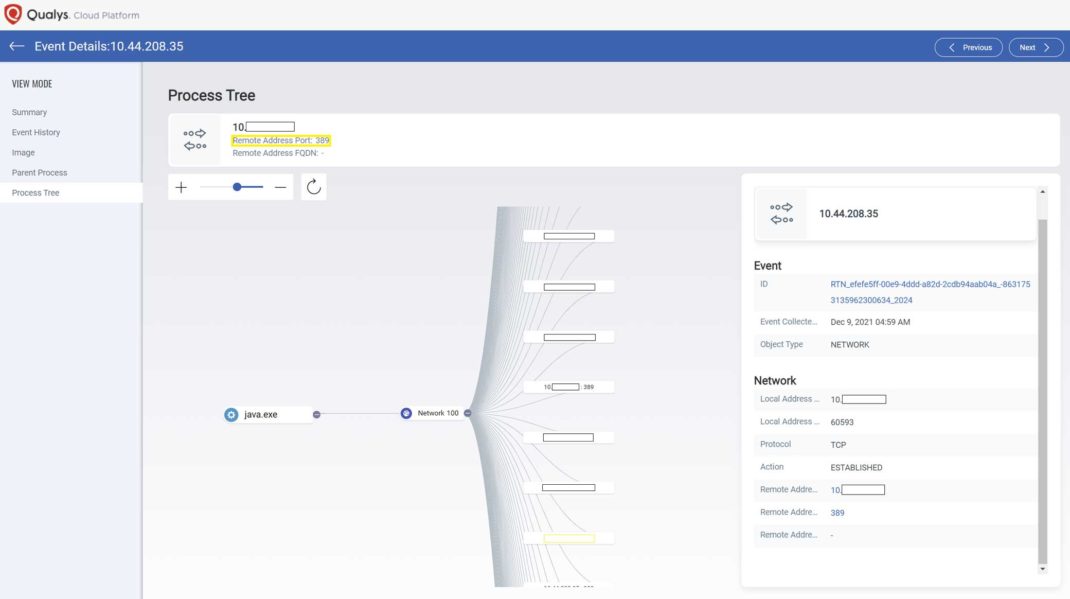
Log4Shell Exploit Detection and Response with Qualys Multi-V - vulnerability database
MORE

website/links.json at gh-pages · academia-de-ursarie/website · GitHub

website/links.json at gh-pages · academia-de-ursarie/website · GitHub

Microsoft Office Vulnerabilities Used to Distribute FELIXROO - vulnerability database

Microsoft Word - .RTF Remote Code Execution - exploit database

website/links.json at gh-pages · academia-de-ursarie/website · GitHub

PDF) Cross-platform C# programming for iOS, Android, and Windows Phone Creating Mobile Apps with Xamarin.Forms

Dropping Files on a Domain Controller Using CVE-2021-43893 - vulnerability database

website/links.json at gh-pages · academia-de-ursarie/website · GitHub
TwitterRecommenderSystem/database.json at master · ravinkohli/TwitterRecommenderSystem · GitHub

How Akamai Can Help You Fight the Latest Exploitation Attemp - vulnerability database












/cdn.vox-cdn.com/uploads/chorus_asset/file/22506481/Screen_Shot_2021_05_11_at_10.09.26_AM.png)

